Integrating OWASP into Software Development Lifecycle
It has been quite some time since I’ve been contemplating publishing an article on the Secure Software Development Lifecycle. This article aims to provide valuable insights for individuals seeking to integrate security into their development environments or considering the adoption of secure coding practices.
In today’s dynamic digital environment, Agile Software Development Lifecycle (SDLC) methodologies have emerged as the foundation of numerous software projects. Agile’s emphasis on flexibility, adaptability, and accelerated time-to-market empowers teams to swiftly address evolving requirements and consistently deliver top-tier software. Yet, amidst this rapid pace and agility, security considerations can sometimes be sidelined, exposing systems to potential cyber threats.
To meet this challenge head-on, integrating security practices into the Agile SDLC becomes indispensable. The Open Web Application Security Project (OWASP) stands out as a trusted authority in ensuring robust security measures. OWASP offers a wealth of resources, tools, and best practices specifically designed to assist developers in constructing secure applications. By seamlessly integrating OWASP into the Agile SDLC, not only does it fortify the software’s security stance, but it also cultivates a proactive ethos towards addressing security concerns at every stage of the development journey.
Embed security practices into your SDLC by integrating security activities at each phase, including planning, design, development, testing, deployment, and maintenance. Ensure that security requirements are defined, implemented, and verified throughout the development lifecycle.
In this article we will focus more about following topics:
- Early Security Awareness
- OWASP Top 10 validations for any new enhancements/ existing codebase
- Adapting Secure Coding practices
- Security Reviews in every sprint cycle
Early Security Awareness: Start by fostering a culture of security awareness within the Agile team. Educate team members about common security vulnerabilities, such as injection attacks, cross-site scripting (XSS), and security misconfigurations. OWASP’s documentation and training materials can serve as valuable resources for this purpose.
Incorporate security requirements and user stories into the product backlog alongside functional requirements.
OWASP Top 10 Validations: Prepare the list of OWASP Top 10 verification guide for developer to understand the technicality of vulnerability how it can be exploited, what are weakness in the codebase, how attackers take the leverage of this weakness and how to mitigate such flaws.
Provide developers with code samples, libraries, and frameworks that facilitate secure coding practices and help mitigate common vulnerabilities.
At the start of every Sprint cycle, it’s crucial for Technical Leads and Product Owners to give developers an OWASP verification guide. This guide helps developers follow security best practices and keep up with the latest standards while working on new features or improvements. Providing this guide upfront ensures that teams prioritize security from the beginning of the development process.
Define security acceptance criteria for each user story to ensure that security considerations are addressed during development and testing.
Adapting Secure Coding Practices: Encourage developers to follow the OWASP secure coding practices. Evaluate current development processes, coding practices, and security measures. Identify any gaps or weaknesses in your security posture that need to be addressed.
Develop and enforce secure coding standards based on OWASP guidelines, industry best practices, and organizational requirements. Define coding conventions, patterns, and practices that promote secure coding and minimize the risk of vulnerabilities.
e.g., Input Validation, Authentication and Session Management, Secure Communications, Error Handling, Access Controls,
Security Review: For a pragmatic strategy, consider incorporating an additional task within the Epic/Story, assigning a knowledgeable reviewer well-versed in OWASP security standards. This reviewer can meticulously scrutinize the code against OWASP Top 10 security controls prior to approving pull requests or code merges. Upon completion of the verification process, furnish feedback to the developer accordingly. Furthermore, in the event of identifying critical security gaps, it is prudent to halt deployments. Developers should then address these issues before proceeding with PR approvals, ensuring a robust security posture before deployment.
Integrate security testing seamlessly into the Agile development cycle. Implement techniques such as Static Application Security Testing (SAST), Dynamic Application Security Testing (DAST), and Interactive Application Security Testing (IAST) to continuously assess the security posture of the application.
By integrating OWASP best practices into Agile SDLC, organizations can effectively mitigate security risks and build robust, secure software products. This approach not only strengthens the resilience of applications against cyber threats but also instills a security-first mindset within the Agile development team. Remember, in the ever-evolving landscape of cybersecurity, proactive measures are key to staying one step ahead of potential threats.
Below is a simplified illustrating the key stages and activities:
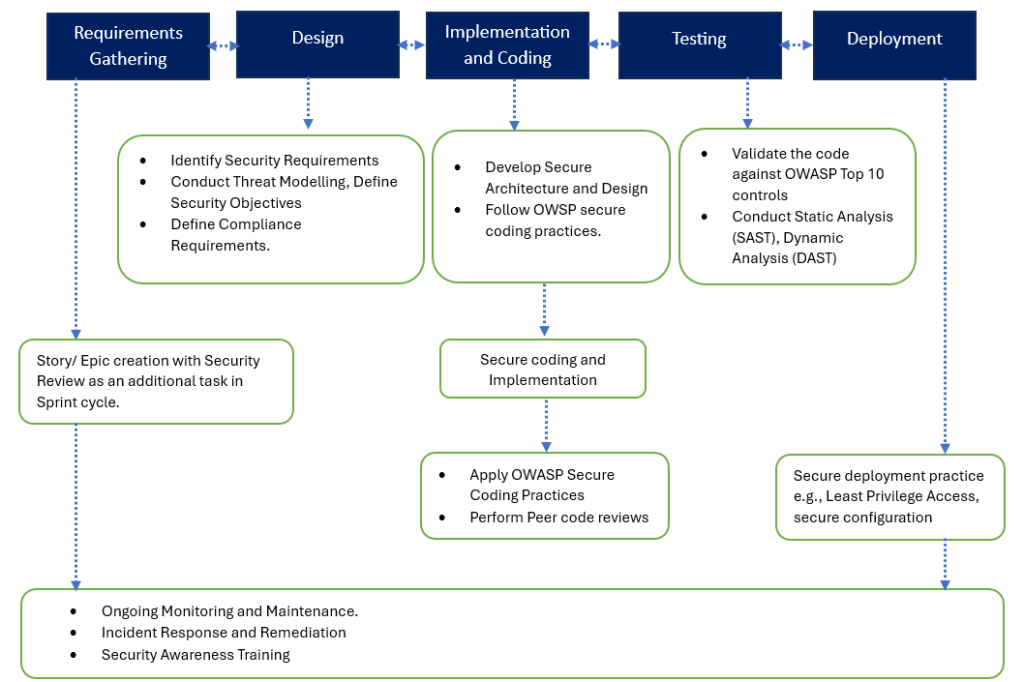
Key note: Highly recommend considering the adoption of either OWASP SAMM 2.0 or ASVS 4.0.3 for enhancing your organization’s security posture. Both frameworks offer comprehensive guidance and best practices tailored to different aspects of application security. Whether you’re focused on improving your security maturity level with OWASP SAMM or ensuring adherence to rigorous security standards with ASVS, integrating these frameworks into your development processes can significantly bolster your defenses against cyber threats.